Which Answer Best Describes the Accountability Component of Access Control
It consists of two main components. Question 8 of 10 100 Points Which answer best describes the identification component of access control.
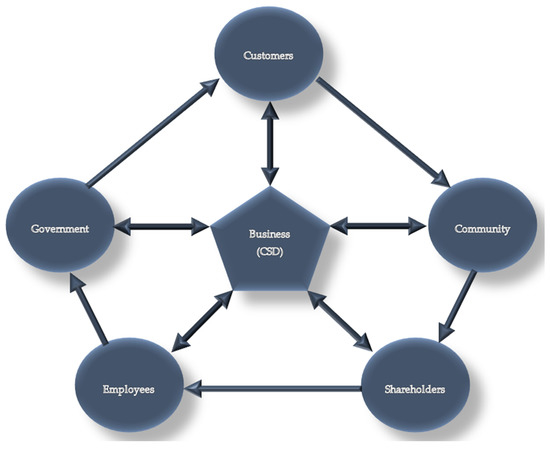
Sustainability Free Full Text The Relationship Between Corporate Sustainability Disclosure And Firm Financial Performance In Johannesburg Stock Exchange Jse Listed Mining Companies Html
Accountability is the concept of answerability by an individual or a department for the performance or outcomes of specific activities.

. Meet the goals of the organizations security policy. What is physical access control. Accountability is the method a subject uses to.
Low Water-Mark Mandatory Access Control. Which of the following is the best example of capabilities tables. Which answer best describes the accountability component of access control.
It has five principles pertaining to setting the tone at the top demonstrating a commitment to competence and establishing oversight structure responsibility and enforcing accountability. MAC is more secure and less flexible than DAC. Answers A B and D are not associated with labels.
The process of identifying users who seek access to secure information. AnswerRBAC Role Based Access Control Role-Based-Access-Control RBAC is a policy neutral access control mechanism defined around roles and privileges. AIdentification is the validation or proof that the subject requesting access is indeed the same subject who has been granted that access.
The logging of access and usage of information resources. Which answer best describes the accountability component of access control. Essentially the accountable party is responsible for the execution of the desired role.
AA virus that changes its code as it delivers the infection. Physical access control is a set of policies to control who is granted access to a physical location. The components of RBAC such as role-permissions user-role and role-role relationships make it simple to do user assignments.
Which answer best describes the accountability component of access control. D Improved control of Service Assets and Configurations. A Meet the goals of the organizations security policy.
Logical access control tools are used for credentials validation authorization and accountability in an infrastructure and the systems within. Authorization is the third step of access control. Accountability Each step from identity presentation through authentication and authorization is logged.
Accountability is the process of creating and maintaining the policies and procedures necessary to ensure proper information is available when an organization is audited. This type of access control can also be embedded inside an application operating system database or. B Improved quality of Service.
Which of the following best describes a rootkit. Further the object or some external resource logs all activity between the subject and object. Access control is paramount for security and fatal for.
BReplicates itself over a network to infect computers and devices. The process of tracing actions to their source. Labels are associated with Mandatory Access Control MAC.
The security kernel enforces access control of computer systems. Authentication and authorization says Daniel Crowley head of research for IBMs X-Force Red which focuses on data security. The configuring of the Security log to record events.
If access is not specifically granted it is forbidden. Accountability is the method a subject uses to request access to a. It is considered prohibitive.
The principal party delegates roles to other parties but remains liable if an action is not executed well or in the event of a loss. Authentication is all about proving or verifying that someone is who they claim to be. Q2 Which statement best describes DAC Discretionary Access Control.
Q1 Identify the three 3 security functions associated with AAA. These components enforce access control measures for systems applications processes and information. In fact the control environment is the foundation.
Authentication is a technique used. Identification is the method a subject uses to request access to a system. Access controls are policies or procedures used to control access to certain items.
Authentication and Access control. Real-world examples of physical access control include the. Often embedded in the object itself this process enforces least privilege need-to-know and separation of duties as defined in Chapter 1.
LOMAC is a security enhancement for Linux that uses Low Water-Mark Mandatory Access Control to protect the integrity of processes and data from viruses Trojan horses malicious remote users and compromised root. High Water-Mark Mandatory Access Control. Brenda a freelance writer revises and edits her own work a number of times while it is still in progress.
MAC is not permissive. Authentication and authorization are key components of information security cybersecurity and access control. C A program that easily can hide and allow someone to take full control of your computer from a remote location.
Although this article focuses on information access control physical access control is a useful comparison for understanding the overall concept. Asked Dec 28 2016 in Computer Science Information Technology by Oldcrow. Accountability is the validation or proof that the subject requesting access is indeed the same subject who has been granted that access.
Theyre also integral to identity and access management. Q3 Which is an example of technical. C Makes sure that IT Services stay aligned to business requirements.
Accountability is the validation or proof that the subject requesting access is indeed the same subject who has been granted that access. Access control systems grants access to resources only to users whose identity has been proved and having the required permissions. Think of the difference between parents who set and enforce house rules on things like homework.
Which form of access control has a many-to-many relationship and makes use of mapping between a user and a subset of goals. Each object folder or file has an owner and the owner defines the rights and privilege. To accomplish that we need to follow three steps.
Physical access controls deter physical access to resources such as buildings or.

Agile Teams Scaled Agile Framework

The 6 Privacy Principles Of The Gdpr Privacy Policies

3rd Grade Math Common Core Standards All 3rd Grade Math Review Worksheets Early Finishers 3rd Grade Math Worksheets And Homework
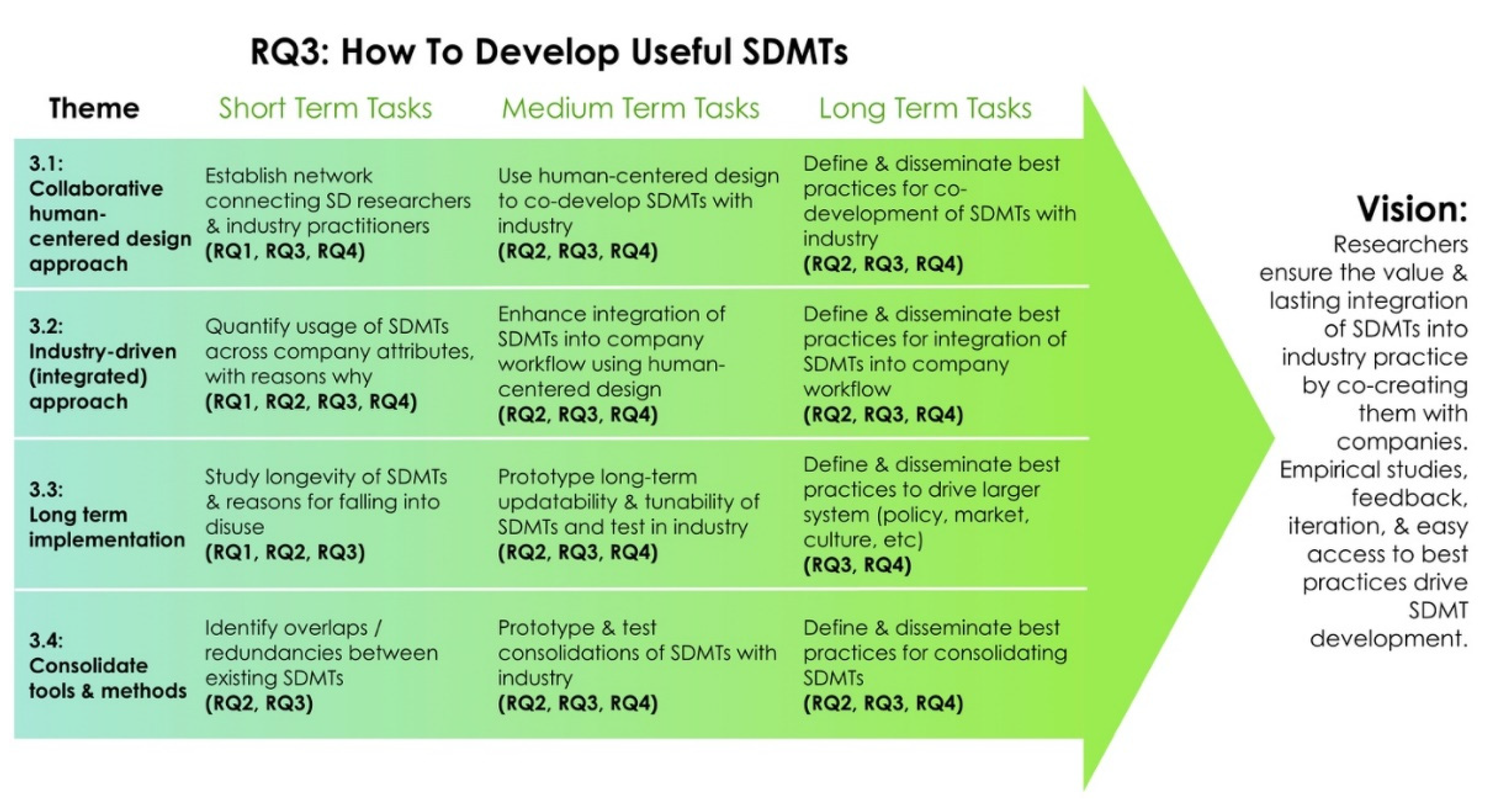
Sustainability Free Full Text A Research Roadmap For Sustainable Design Methods And Tools Html

Web Hosting Company India Http Zine Logbet Com Article Php Id 59883 Web Hosting Pinterest Hosting Company

Web Hosting Company India Http Zine Logbet Com Article Php Id 59883 Web Hosting Pinterest Hosting Company

Availability Management It Process Wiki

Security Integration Cloud Adoption Framework Microsoft Docs
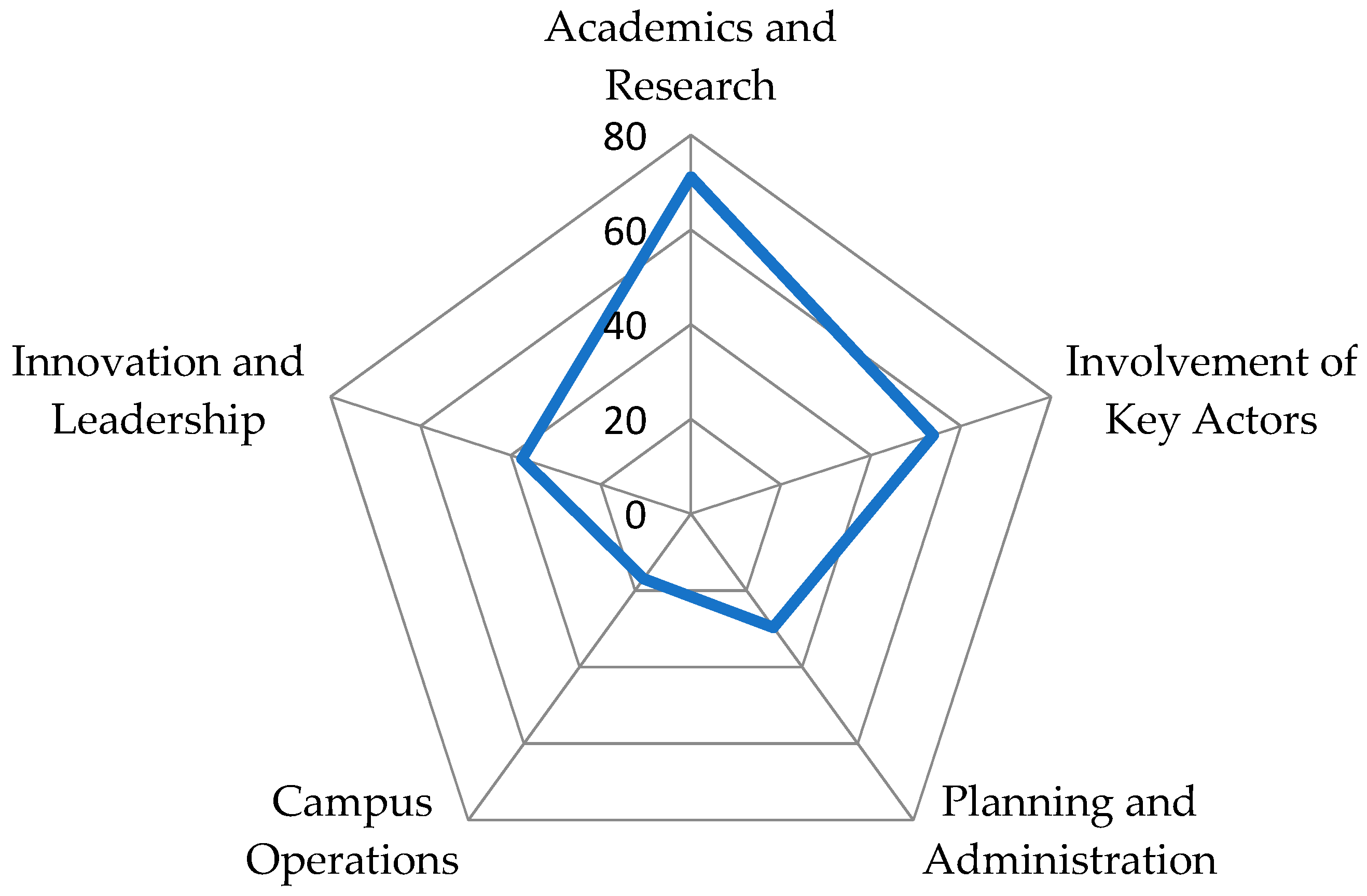
Sustainability Free Full Text Sustainability Assessment And Benchmarking In Higher Education Institutions A Critical Reflection Html
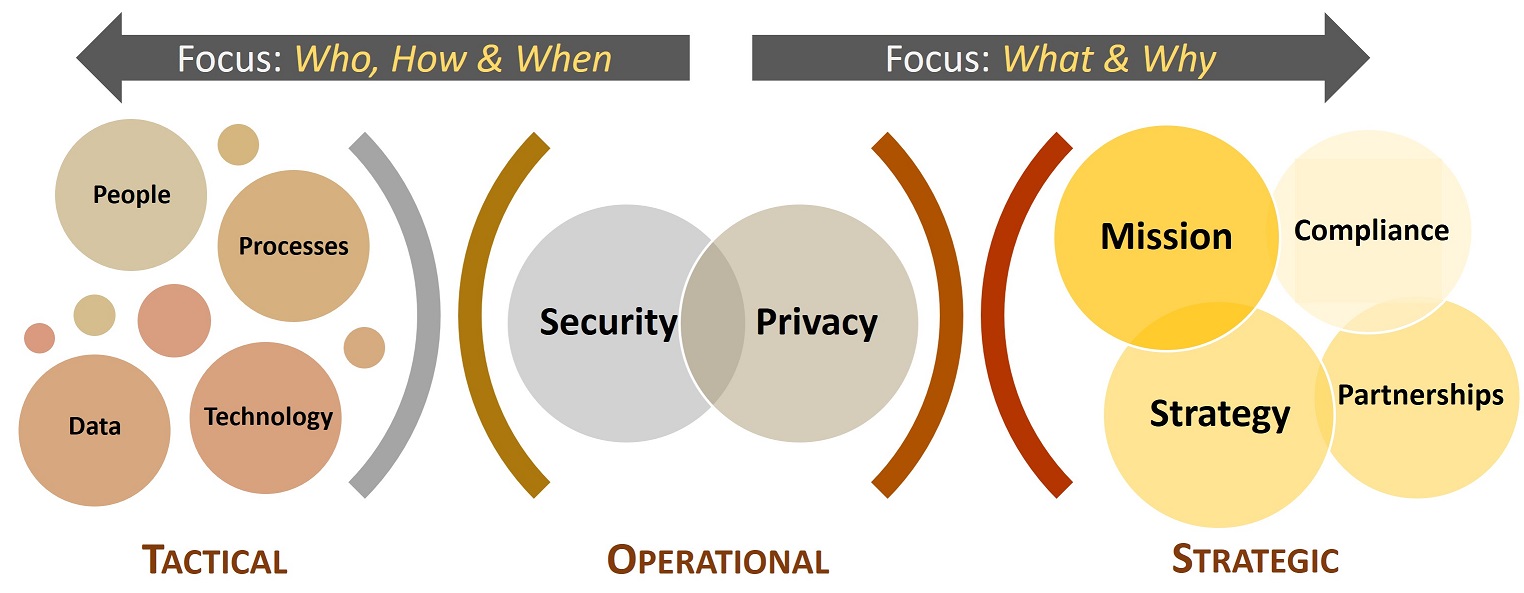
Policies Vs Standards Vs Controls Vs Procedures

Good Governance Definition And Characteristics Uclg Aspac

3rd Grade Math Common Core Standards All 3rd Grade Math Review Worksheets Early Finishers 3rd Grade Math Worksheets And Homework
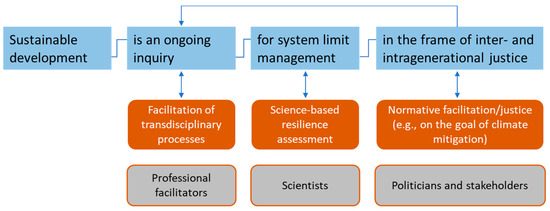
Sustainability Free Full Text Unintended Side Effects Of Digital Transition Perspectives Of Japanese Experts Html

Web Hosting Company India Http Zine Logbet Com Article Php Id 59883 Web Hosting Pinterest Hosting Company
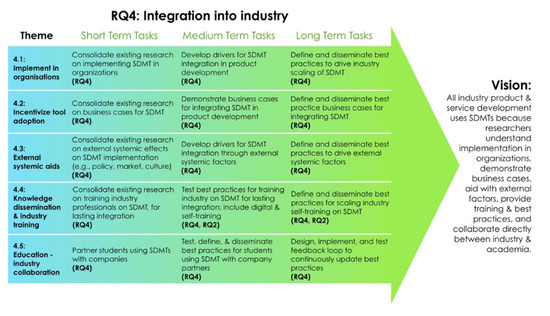
Sustainability Free Full Text A Research Roadmap For Sustainable Design Methods And Tools Html


Comments
Post a Comment